On Nov.30th, China’s influential media Jinse Finance has published an exclusive review about DxChain, talking about data security and how DxChain build a new data security ecosystem. Please refer down below for this interview.
At the age of the Internet in the past decade, data breach issues — whether in Silicon Valley or in China — remain unsolved. Now, the distributed storage enabled by blockchain is believed to the next breakthrough technology to improve data security.

Data leak is out of control
On August 28, Chinese media reported that personal information and data in hotels owned by Huazhu Hotels Group have been leaked. Someone was selling 130 million hotel guest data packages on the dark web, containing a total of 500 million data pieces. These data include registration information on the Huazhu official website, hotel check-in information, and hotel records, along with personal information like names, ID number, home address, internal ID number, and 130 million ID cards.
“If we think about the data breach in Huazhu hotels, we can find that the scope of the leaked data may be concentrated on young Chinese who work away from their home,” Allan Zhang, founder of DxChain, a Silicon Valley-based blockchain startup, told Golden Finance.
Some of the recently reported data breaches are staggering. On September 28, Facebook said their website was under attacks by hackers, exposing the personal information of nearly 50 million users. The social media giant was also plagued with the Facebook-Cambridge Analytica data scandal this March — Cambridge Analytica had obtained the personal data of millions of Facebook users without their consent.
On November 2, HSBC, officially known as The Hong Kong and Shanghai Banking Corporation Limited, announced that some of their customer accounts had been accessed by unauthorized users between October 4–14. The bank immediately suspended their online access, sent notifications to customers whose accounts may have experienced unauthorized access via phones and emails, and helped them change their digital and mobile access.
Said one source who is familiar with the incident, this data leak was caused by the so-called “hitting the database” attack and was estimated to affect about 1 percent of USBC’s US accounts. The information breached may include full name, mailing address, phone number, email address, date of birth, account numbers, account types, account balances, transaction history, payee account information, and statement history where available. HSBC said in a statement that they will offer affected customers one year of credit monitoring and identity theft protection service.

“From Silicon Valley to China, many companies have tried a lot of solutions for data breaches, but they have not been completely successful,” Allan adds.
The aim of DxChain is to build an ecosystem for the data industry on the foundation of data security. We are living in a world where the rapid increases in the level of informatization play a great role. We receive mind-boggling amounts of data on a daily basis in different ways. These data promise a great business value.
Why data protection is necessary?
The importance of data protection varies from different perspectives. But why data protection is needed and what is its consequence? Below is Allan’s detailed explanation.
In the world where the Internet is everywhere, giant companies’ products have seeped into our lives in every aspect. Behind the huge success of those tech giants — Facebook, Google, Amazon in the US, and Baidu, Alibaba, and Tencent in China — is data.
Data is the new oil in modern society. The data generated in our lives, including consumption records, behavioral messages, mobile phone installation software, friends, and other data, have great potential, particularly for giant companies.
For example, Tencent’s social products play a great role as a source of data, which, after being pre-processed and matched, contributes to a deep correlation with Tencent’s other services. Data is particularly important for Tencent’s business partners also. WeChat’s collected data is believed to improve shopping recommendations and internet advertisings from JD.com, China’s second largest e-commerce company, which has joined forces with Tencent.
Tech giants need data. Same with other Internet companies.
Now the problem is: Both tech giants and SMEs have an adequate level of data protection, but their staff can easily access and download data without decrypting it, which leads to under-the-table incomes and increases the risk of data breach.
Another threat comes from hackers. They are motivated by profits and breach the defenses of data security systems. “So, for the data of the company’s internal servers, no matter how good the operation and maintenance team protection is claimed, how the backup is used and how the technicians are trained, it is difficult to prevent data security problems,” Allan says.
Insights on data security
The development of the Internet begins with electronic computers. Then it is the local area network interconnects computers in a limited area. The World Wide Web connects laptops and desktop computers via fixed-line services and mobile internet provides access to Internet services for handheld mobile devices. Today, we are witnessing the growth of Internet-of-things (IoT).
At the age of the IoT, each accessed node are regarded as data generators, and others are data buyers and data collectors.
Data is the core competence for Internet companies. For example, the rapid development of AI technology is attributed to deep learning and a massive amount of available data. “The fate of an Internet company is increasingly dependent on data,” Allan adds.
Companies can choose data, or choose a reliable security solution to protect their data. But for users, as long as they live in an information society, they can neither owe data nor effectively protect their data. The users’ dependence on each company’s products and services will make the collection of data more concentrated. Due to the Matthew effect, once a company’s data is leaked, it will suffer a significant financial loss.
“At present, it is necessary to protect the company that has the capabilities of data collection and storage, and to give the data ownership and rights back to data generators.”
How DxChain addresses data security issues
Allan Zhang says DxChain uses a multi-chain structure: The master chain is designed to package, verify, and deliver smart contracts; The data storage side-chain has data storage capability, and the computing side-chain deals with transactions and sends the result back to the master chain for verification.
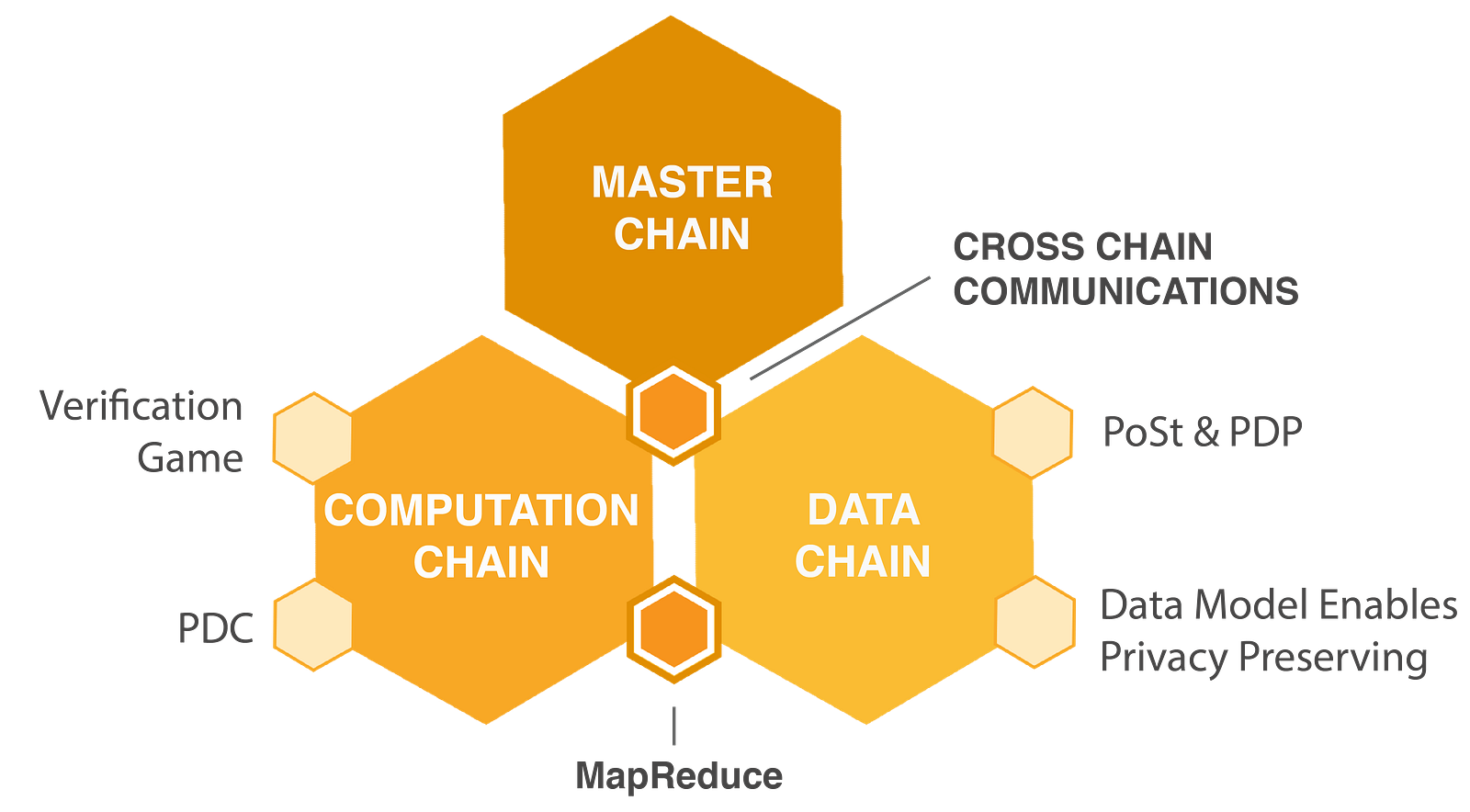
The theoretical model of DxChain can be fully verified in this structural design. When a user uploads their data through a data storage method akin to Baidu’s cloud service Wangpan, DxChain divides the data into small blocks and encrypts each block by using an encryption algorithm along with a key. Eventually, each encrypted data block and its key are concurrently stored in the chain. The data ownership is also given back to its data producer who can use the private key to decrypt the data.
On DxChain, data management can be coded into a smart contract. When data buyers and collectors need data, they can contact the data producer via smart contracts, which take effect once the two parties reach a certain agreement. The right to use the data is later transferred to data consumers, but the data ownership is still in the hands of the data producer.
In this way, even if hackers have obtained the encrypted data package through attacks, they cannot use the data without having an authorized private key. And each package has encryption. The decryption workload for a large amount of data is increasingly heavy, and the attack cost rises linearly.
DxChain also has an elaborate design that stands out among its features: It puts an asset layer on the periphery of the data layer. Data and assets are encrypted by the encryption method of the wallet. If hackers decrypt the wallet, they only obtain the assets that can be taken away. Compared to hackers’ appeal, this design can let hackers ignore data.
Under this comprehensive design, Allan told Golden Finance the ecosystem DxChain intends to build.

“In DxChain, there are no monopolies, but more individual data producers who exchange data through smart contracts and token transactions. For example, if Huazhu Hotels Group needs data from a user, with the help of smart contracts, the user agrees to share their data, while Huazhu does not have the ownership and the right to use.”
DxChain claims their users can enjoy a friction-less experience of uploading their data, just like uploading data to a cloud storage. DxChain is also planning to provide a large number of economic incentives for different nodes or miners. “If in a P2P network, a node’s data packet has 10 backup files stored in the node, but 5 of the backup files cannot be queried, to ensure the number of backups and the transfer efficiency, more nodes are needed to deploy the backup. The master chain will carry out an incentive strategy to help generate more backups,” Allan explains. This is also a problem that remains unsolved in the P2P storage network. Under the incentive mechanism of the blockchain, this solution is now plausible.
Conclusion
DxChain’s test network version Alpha has been launched in September. The master chain’s ability to produce blocks is stable, and the storage sidechain version Beta is being tested internally. Allan also reveals that to adapt DxChain’s behavior in the face of changing environments, DxChain’s master chain and side-chains are deployed in one development stack, so that each node can select the function from this node and be more flexible to achieve development goals. At the same time, DxChain can also adjust the ability of miners in each deployment node to provide storage, computing, verification, and other functions.
As a data security expert, Allan believes the future of the data security industry bright. He tells Golden Finance that “data security solutions, especially for data breaches, have been done in the industry for many years, but they are not successful enough. The blockchain technology is believed to be revolutionary to data security because, from the perspective of cryptography and IT technology, the technology is convincing. Data security is the bottleneck in many industries, and data-based blockchains can really solve the problem.”
